SSH: The Secure Shell That Protects Your Data!
Secure Shell (SSH) is an essential way to connect to a remote server securely. SSH provides secure remote access to computers and servers. Whether you’re a system administrator, a developer, or just someone who values online privacy, understanding SSH is crucial.
This article will introduce you to SSH and explore its significance.
The Basics of SSH
At its core, SSH is a cryptographic network protocol that provides a secure channel over an unsecured network. Think of it as a tunnel that encrypts your data in transit, making it unreadable to prying eyes. Your computer will make an SSH connection from one location to another, this allows you to connect and manage the remote computer as if you were sat locally at the terminal. These servers can be located anywhere in the world.

Key Uses of SSH
SSH has a wide range of applications; the most popular include:

Secure Remote Access:
SSH allows users to securely log into remote systems, such as servers or other computers, over the internet. This is crucial for system administration, troubleshooting, and managing remote resources.

Secure File Transfer:
SSH enables the secure transfer of files between systems using protocols like SFTP (SSH File Transfer Protocol) or SCP (Secure Copy). This ensures data confidentiality and integrity during transmission.

Secure Command Execution:
SSH allows users to execute commands on remote systems securely. This is essential for remote administration tasks, software updates, and configuration management.

Port Forwarding:
SSH can be used to create secure tunnels for forwarding network traffic from one port to another. This is useful for bypassing firewalls, accessing restricted services, and securing network connections.

Authentication and Key Management:
SSH supports various authentication methods, including passwords and public key authentication. Public key authentication is considered more secure and is often used for automating tasks and managing access to multiple systems.

Virtual Private Networks (VPNs):
SSH can be used to create ad hoc VPNs, providing a secure and encrypted connection over the Internet for protecting sensitive data and accessing private networks.
How Does SSH Work?
SSH utilizes public-key cryptography for authentication and symmetric encryption for data transmission. Here’s a simplified breakdown:
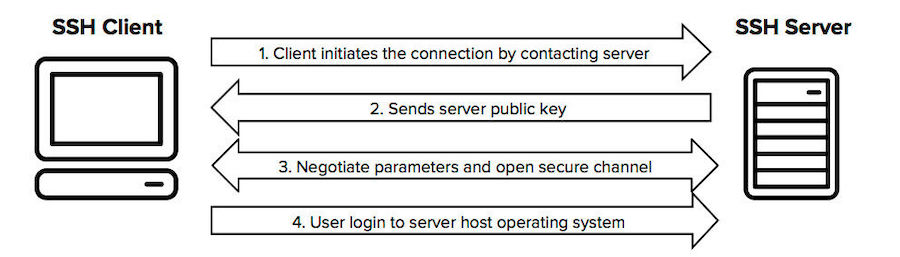

Authentication:
You generate a public-private key pair. The public key is shared with the remote server, and the private key remains on your computer. The server challenges your client, which responds with a signature created using your private key.
Encryption:
Once authenticated, SSH establishes a secure session using symmetric encryption algorithms. Data is encrypted before it leaves your computer and decrypted only upon arrival at the destination.
| Public-Key Cryptography: | Used for verifying the user’s identity. Like a digital signature, proves you have the right “key” without revealing it. |
| Symmetric Encryption: | Used to scramble the data you send back and forth. Fast and efficient, ideal for large amounts of data. Common algorithms: AES, ChaCha20-Poly1305 |
| Hashing: | Creates a unique “fingerprint” of your data. Used to check if the data has been changed during transmission. |
| Key Exchange Algorithms: | A secure way to agree on the secret code used for symmetric encryption. Like whispering a secret in a crowded room, only you and the server can hear it. |
Why Choose SSH?
SSH offers numerous advantages over traditional remote access methods like Telnet:
- Strong Security: Encryption protects your data from unauthorized access.
- Authentication: Public-key cryptography ensures only authorized users can connect.
- Versatility: SSH supports a wide range of commands and protocols.
- Open Standard: SSH is well-documented and widely adopted.

How to use SSH
To use SSH, you’ll typically need an SSH client (e.g., OpenSSH) on your computer and an SSH server running on the remote machine.
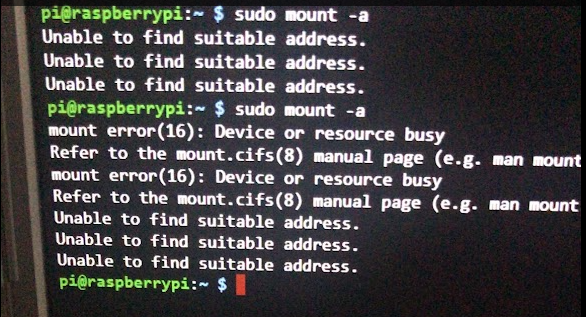
ssh username@hostnameThe most basic command. Connects to a remote server with the specified username and hostname (or IP address)
ssh -p port username@hostnameConnect to a server on a non-standard port (the default is port 22)
ssh -i identity_file username@hostnameAuthenticate using a private key file instead of a password.
ssh -L local_port:remote_host:remote_port username@hostnameSet up local port forwarding
ssh -R remote_port:local_host:local_port username@hostnameSet up remote port forwarding
ssh -X username@hostnameEnable X11 forwarding (graphical applications).
Like this procedure, check out our other Tech Quickys




Recent Comments