RDS SSL Certificate Rotation: Everything You Need to Know for a Smooth Transition
Amazon RDS SSL CA certificates rds-ca-2019 are expiring soon. To maintain secure connections, switch to new CA certificates: rds-ca-rsa2048-g1, rds-ca-rsa4096-g1, or rds-ca-ecc384-g1. This guide outlines the steps to update your clients or applications and RDS certificates.
RDS SSL/TLS Certificate Rotation Guide for Amazon RDS
Amazon RDS provides the following CA’s to sign the DB server certificate for a DB instance.
| Certificate authority (CA) | Description |
|---|---|
| rds-ca-2019 | Uses a certificate authority with RSA 2048 private key algorithm and SHA256 signing algorithm. This CA expires in 2024 and doesn’t support automatic server certificate rotation. If you are using this CA and want to keep the same standard, we recommend that you switch to the rds-ca-rsa2048-g1 CA. |
| rds-ca-rsa2048-g1 | Uses a certificate authority with RSA 2048 private key algorithm and SHA256 signing algorithm in most AWS Regions. In the AWS GovCloud (US) Regions, this CA uses a certificate authority with RSA 2048 private key algorithm and SHA384 signing algorithm. This CA remains valid for longer than the rds-ca-2019 CA. This CA supports automatic server certificate rotation. |
| rds-ca-rsa4096-g1 | Uses a certificate authority with RSA 4096 private key algorithm and SHA384 signing algorithm. This CA supports automatic server certificate rotation. |
| rds-ca-ecc384-g1 | Uses a certificate authority with ECC 384 private key algorithm and SHA384 signing algorithm. This CA supports automatic server certificate rotation. |
This can also be done via the AWS-CLI
aws rds describe-db-engine-versions --default-only --engine postgresPreparing for RDS SSL Update
- Update Before Rotation: Update clients or applications connecting to RDS databases before rotating certificates. You will likely need to update them with the latest RDS global certificates found here.
- New CA Certificates: Refer to AWS documentation for details on new certificates and supported regions.
- RDS Proxy: No update is required for applications using RDS Proxy connections. (if applicable)
- Go Version 1.15: Update the certificate if using a Go version 1.15 application that had the rds-ca-2019 certificate before July 28, 2020. (if applicable)
Updating Your Clients or Applications for RDS SSL
- Download the New Certificate: Download the new SSL/TLS certificate as per the documentation.
- Update Applications: Collaborate with application developers to update the SSL/TLS certificates within your applications.
- Specific DB Engines: Follow the documentation for updating applications for various DB engines, including MariaDB, Microsoft SQL Server, MySQL, Oracle, and PostgreSQL.
- Certificate Bundle: Use the provided certificate bundle to maintain connectivity during the transition.
Step-by-Step Procedure
Step 1 – Preparing for the Update
- Backup: Create a snapshot or automated backup of your RDS instance.
- Communication: Inform relevant stakeholders (developers, system administrators, etc.) about the planned update and potential downtime.
- Test Environment: If possible, replicate your production environment for testing to minimize risks.
Step 2 – Update Clients
- Download Certificate: Download the new RDS certificate bundle from AWS documentation.
- Configuration: Update your application’s configuration to reference the new certificate’s location.
- MySQL Client Libraries: If using MySQL, ensure your client libraries are up-to-date and compatible with the new certificate.
- Thorough Testing: Test your application in the non-production environment to validate functionality and connections.
Step 3 – Update RDS Certificates
- Log in to AWS Management Console: Navigate to the RDS section.
- Select the RDS Instance: Choose the DB instance to modify.
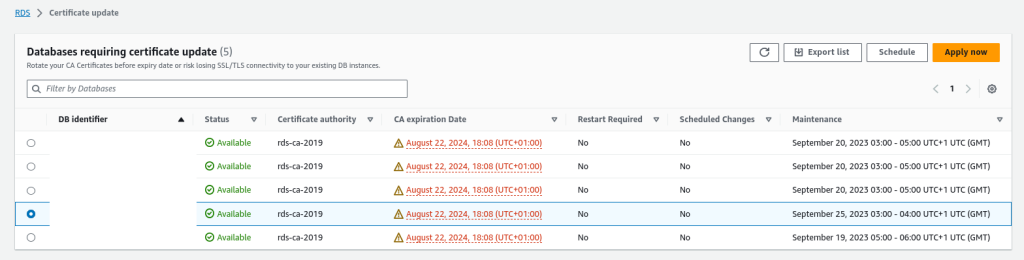
- Initiate Modification: Click on the Modify button.
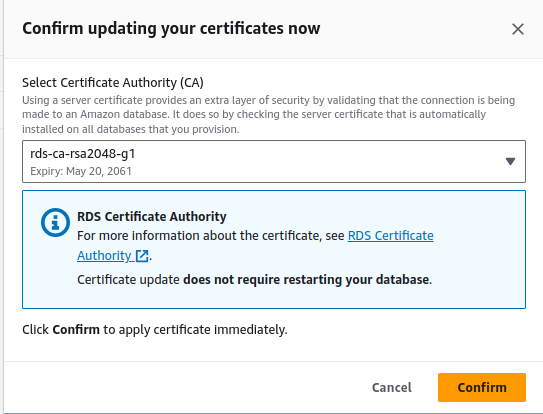
- Update CA Certificate: Change the CA to the new certificate.
- Apply Changes immediately or schedule them for the next maintenance window.
- Monitor RDS Instance: Monitor the RDS instance for any issues.
Step 4 – Post-Update
- RDS Monitoring: Use CloudWatch metrics to monitor your RDS instance for any connection errors or performance issues.
- Application Monitoring: Monitor your application logs for any unexpected behavior or errors related to the certificate change.
- Roll Back Plan: Have a rollback plan in place in case of unforeseen problems.
Ansible Script to pull all this information from your AWS Account
Note:
- Make sure you configure your AWS_ACCESS_KEY and SECURE_TOKEN in your local console.
- Make sure you change the value for your ECS Clusters.
- name: Get ECS Task Details
ignore_errors: true
hosts: localhost
tasks:
- name: List All Task ARNs in the Cluster
shell: "aws ecs list-tasks --cluster ecs-cluster-prod"
register: task_list
- name: Get Details of Each Task
shell: "aws ecs describe-tasks --cluster ecs-cluster-prod --tasks {{ task_list.stdout | from_json | json_query('taskArns[]') | join(' ') }}"
register: task_details
- name: Extract Task Details
set_fact:
task_info: "{{ task_details.stdout | from_json | json_query('tasks[*].{Name: taskDefinitionArn, Group: group, Image: containers[0].image, PrivateIP: containers[0].networkInterfaces[0].privateIpv4Address}') }}"
- name: Get Load Balancer Details
shell: "aws ecs describe-services --cluster ecs-cluster-qa --services {{ item | regex_replace('service:', '') }}"
register: service_details
loop: "{{ task_details.stdout | from_json | json_query('tasks[*].group') | map('regex_replace', '^task:', '') | list }}"
- name: Display Task Details
debug:
msg: "{{ task_info }}"
- name: Extract Load Balancer Details
set_fact:
lb_info: "{{ service_details.results | map(attribute='stdout') | map('from_json') | map('json_query', \"services[0].loadBalancers[0].{ContainerName: containerName, ContainerPort: containerPort, TargetGroupArn: targetGroupArn, }\") }}"
- name: Display Load Balancer Details
debug:
msg: "{{ lb_info }}"
Additional Best Practices:
- Automate: Whenever possible, script the process for future certificate rotations to streamline the process and reduce manual errors.
- Communication: Keep stakeholders informed of the progress and any potential impacts.
- Documentation: Document the steps taken and any issues encountered for future reference.




1 Response
[…] a revolutionary cloud database service. While the service shares some similarities with traditional RDS offerings, it brings a host of features to the table that set it apart. Designed as a fully managed […]