Unveiling the Power of Kali Linux
Kali is a powerful operating system used by cybersecurity professionals and ethical hackers for penetration testing, digital forensics, and network security assessments. This open-source platform is based on Debian Linux and is designed to provide advanced security tools and features for testing and improving the security of computer systems and networks.
This article will dive into what Kali is, why it’s essential, and how it works.

Kali Linux
Its free, open-source penetration testing platform initially released in 2013. It is specifically designed for cybersecurity professionals, hackers, and security enthusiasts who need to test the security of computer systems and networks. It comes preloaded with over 600 security tools and features, including:
- Vulnerability analysis tools
- Exploit frameworks
- Network scanning and analysis tools
- Password cracking tools
- Forensic tools
Kali is a versatile platform that can be used for various cybersecurity purposes. It can be run from a live CD or USB drive or installed as a dedicated operating system on a computer. This flexibility makes it an essential tool for cybersecurity professionals and hackers alike.
A Brief History of Kali
Kali has a rich history dating back to 2006 when it was initially launched as BackTrack Linux. The original BackTrack Linux was a Linux distribution based on the Debian operating system and designed for penetration testing and digital forensics. It quickly gained popularity among cybersecurity professionals, students, and hobbyists, who appreciated its wide range of security tools and ease of use.
In 2013, the BackTrack Linux project was officially discontinued and replaced by Kali . Kali was created by a group of developers known as Offensive Security, who had been involved in developing BackTrack Linux. The new operating system was designed to provide a more streamlined and user-friendly experience, adding new tools and features to improve its overall functionality.
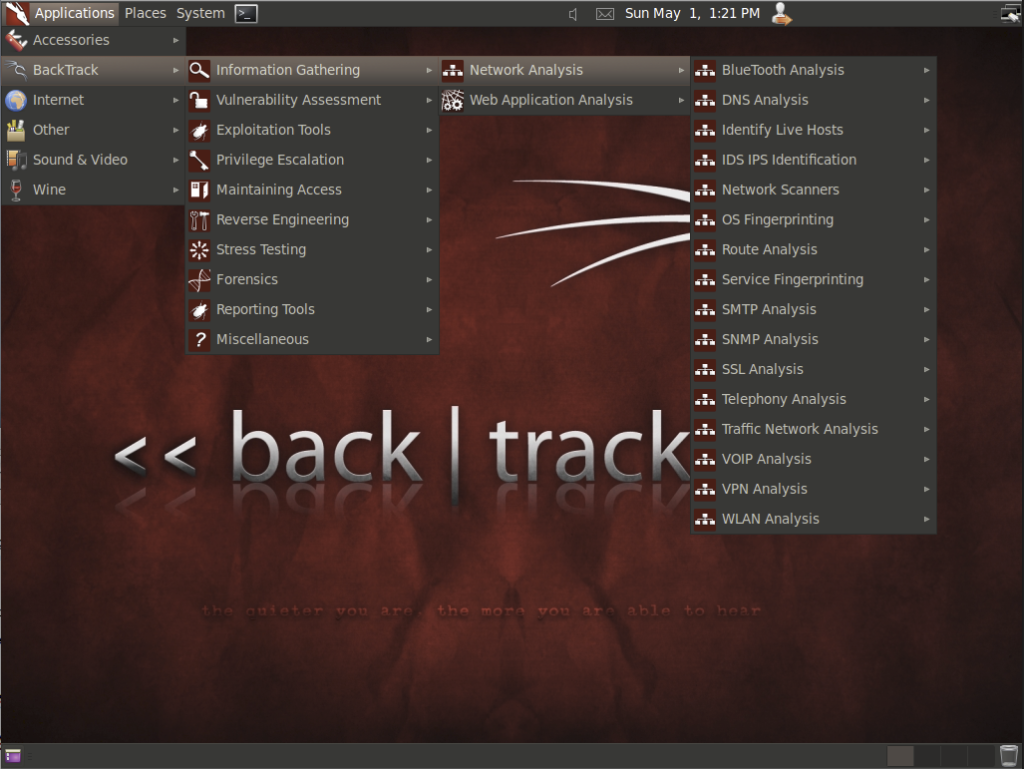
One of the primary goals of Kali was to create an open-source platform that could be used by cybersecurity professionals and enthusiasts around the world. It was also designed to provide a single platform for all cybersecurity tasks, from penetration testing to digital forensics, and everything in between.
Kali has since become one of the most popular cybersecurity platforms in the world, with millions of users around the globe. Its extensive library of tools and applications makes it a valuable resource for cybersecurity professionals, students, and hobbyists alike, and its open-source nature ensures that it will continue to evolve and improve with time.
Today, Kali remains at the forefront of the cybersecurity industry, with new tools and features added regularly to keep up with the latest security threats and trends. Its popularity and success are a testament to the hard work and dedication of its developers and the cybersecurity community as a whole.
Why is Kali important?
Kali is essential for several reasons. Firstly, it provides cybersecurity professionals with powerful tools to test and improve the security of computer systems and networks. This is essential in a world where cyber threats are becoming increasingly common and sophisticated. By using Kali, cybersecurity professionals can identify and address security vulnerabilities before hackers can exploit them.
Secondly, Kali is important because it is a free and open-source platform. This means anyone can download, use, and modify the software to suit their needs. This has led to a vibrant community of developers and users who contribute to the platform by creating new tools, sharing knowledge, and providing support.
Finally, Kali is important because it is constantly evolving. The platform is regularly updated with new features and tools to keep up with cybersecurity threats and trends. This ensures that cybersecurity professionals always have access to the latest tools and techniques for securing computer systems and networks.
How does Kali Linux work?
Kali provides users with a wide range of security tools and features. These tools can be used for various purposes, including vulnerability analysis, network scanning, password cracking, and digital forensics. In addition, Kali is designed to be user-friendly, even for those with little or no experience in cybersecurity.
One of the critical features of Kali is its package manager. This allows users to easily install and manage the many security tools and features included in the platform. The package manager also ensures that all software is up-to-date and secure.
Kali also includes a powerful command-line interface (CLI) that allows users to execute complex commands and scripts. This is particularly useful for advanced users who want to customize and automate their security testing processes.
In addition to its many built-in tools and features, Kali supports using third-party tools and plugins. This means that users can easily integrate their devices and scripts into the platform to extend its functionality.
Best Preinstalled Linux Applications
Kali comes with over 600 preinstalled applications and tools for various cybersecurity purposes. However, some of the most famous Kali applications are:
- Metasploit Framework: A robust exploit development and penetration testing tool for finding vulnerabilities and developing exploits.
- Nmap: A network exploration and security auditing tool for scanning and port mapping.
- John the Ripper: A popular password-cracking tool for testing password strength.
- Wireshark: A network protocol analyzer used for capturing and analyzing network traffic.
- Aircrack-ng: A suite of tools used for testing wireless network security.
- Burp Suite: A web application security testing tool for detecting vulnerabilities in web applications.
- Maltego: A data mining tool for gathering and analyzing information about individuals, organizations, and networks.
- Social Engineering Toolkit (SET): A framework for testing social engineering techniques.
- Hydra: A password-cracking tool used for brute-force attacks against network services.
- Forensic Toolkit (FTK): A digital forensics tool for analyzing and recovering data from computers and digital devices.
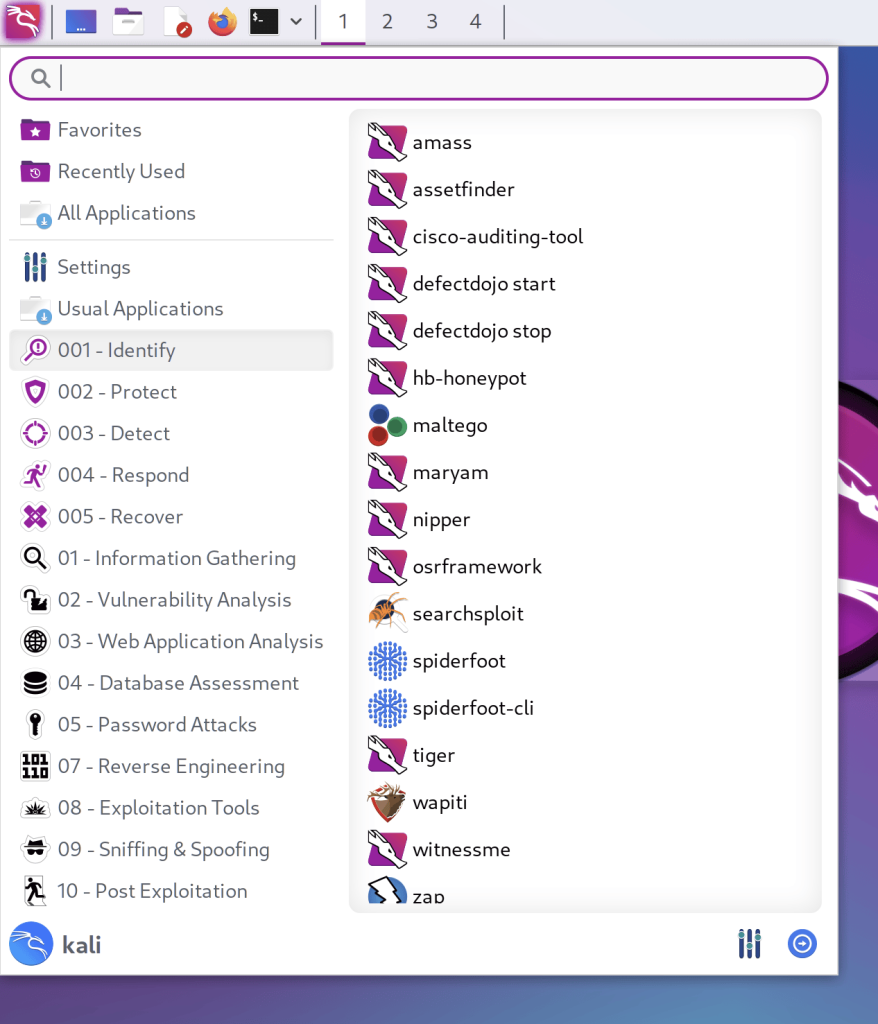
These are just a few examples of the many powerful applications and tools available in Kali Linux. The platform constantly evolves and updates with new features and tools to keep up with the latest cybersecurity threats and trends.
Controversial Kali Linux Apps
Kali is a powerful cybersecurity tool that comes preloaded with hundreds of applications, including some controversial ones. However, it is important to understand that these applications are intended for ethical and legitimate purposes, such as testing and improving computer systems and network security. It is the responsibility of the user to use Kali Linux and its applications in a responsible and ethical manner.
Some of the controversial applications included in Kali are:
- Maltego: While Maltego is a useful data mining tool, it can also be used for social engineering attacks, such as phishing.
- Metasploit Framework: While Metasploit Framework is a powerful tool for finding vulnerabilities and developing exploits, it can also be used for malicious purposes, such as hacking and unauthorized access.
- Aircrack-ng: While Aircrack-ng is a useful tool for testing wireless network security, it can also be used for illegal activities, such as hacking into private wireless networks.
- SET (Social Engineering Toolkit): SET is a powerful framework for testing social engineering techniques, but it can also be used for malicious purposes, such as phishing attacks.
It is important to note that the Kali Linux project does not endorse or condone the use of these applications for illegal or unethical activities. Users should only use Kali Linux and its applications for legitimate and ethical purposes, such as testing and improving computer systems and network security. It is also important to follow all applicable laws and regulations regarding cybersecurity and network security.
Conclusion
In conclusion, Kali is a powerful operating system used by cybersecurity professionals and ethical hackers for testing and improving the security of computer systems and networks. It comes preloaded with over 600 security tools and features, making it a versatile and essential platform for cybersecurity professionals.
Kali Linux is important because it provides a free and open-source platform for cybersecurity professionals and hackers to share knowledge, tools, and techniques. It constantly evolves to keep up with the latest cybersecurity threats and trends, ensuring that users always have access to the latest tools and techniques.
Overall, Kali Linux is an essential tool for anyone involved in cybersecurity or network security. Its flexibility and user-friendly interface make it accessible to users of all skill levels. At the same time, its extensive library of security tools and features provides cybersecurity professionals with the resources they need to keep computer systems and networks secure.
Using Kali Linux can help organizations identify and address security vulnerabilities before they can be exploited by hackers, minimizing the risk of data breaches and other security incidents. It is also a valuable tool for individuals learning more about cybersecurity and ethical hacking.
As Kali Linux continues to evolve and improve, it will likely remain one of the most popular and widely used cybersecurity platforms for years. Its open-source nature and strong community support ensure that it will continue to be a valuable resource for anyone looking to improve their cybersecurity skills and protect their computer systems and networks from cyber threats.
FAQ on What is Kali
Question 1: What is Kali?
Kali Linux is a powerful operating system built for penetration testing and digital forensics. It is based on Debian and includes hundreds of pre-installed tools for ethical hacking, network testing, and security auditing.
Question 2: Who uses Kali Linux?
Security professionals, penetration testers, and ethical hackers primarily use Kali Linux. It is also popular among students and enthusiasts who want to learn more about cybersecurity and ethical hacking.
Question 3: Is Kali Linux legal to use?
Yes, Kali Linux is a legal operating system that is widely used in the cybersecurity industry. However, it is important to note that using Kali Linux to conduct illegal activities, such as hacking into someone’s computer without their permission, is illegal and can result in serious consequences.
Question 4: Can Kali Linux run on any computer?
Kali Linux can run on most computers and devices, including laptops, desktops, and Raspberry Pis. However, checking the system requirements before installing Kali Linux is important to ensure that your computer meets the minimum specifications.
Question 5: How do I get started with Kali Linux?
To get started with Kali Linux, you can download the ISO image from the official website and install it on your computer. You can also run Kali Linux in a virtual machine or use a live USB to try it out without installing it on your computer.


2 Responses
[…] not on the initial list, Kali Linux is a specialized distribution designed for penetration testing and security auditing. It comes with […]
[…] Since 2013, Kali Linux has been leading the way in hacking tools, taking over from BackTrack Linux4546. It comes with over 600 tools, making it a go-to for experts, enthusiasts, and ethical […]